Spot Trace URL Parameter Vulnerability Exposes Device Locations Globally

SPOT devices are satellite GPS trackers that connect to the Globalstar network to transmit location data. A critical IDOR (Insecure Direct Object Reference) vulnerability in SPOT’s notification system exposed location data for devices worldwide through URL parameter enumeration.
URL Structure
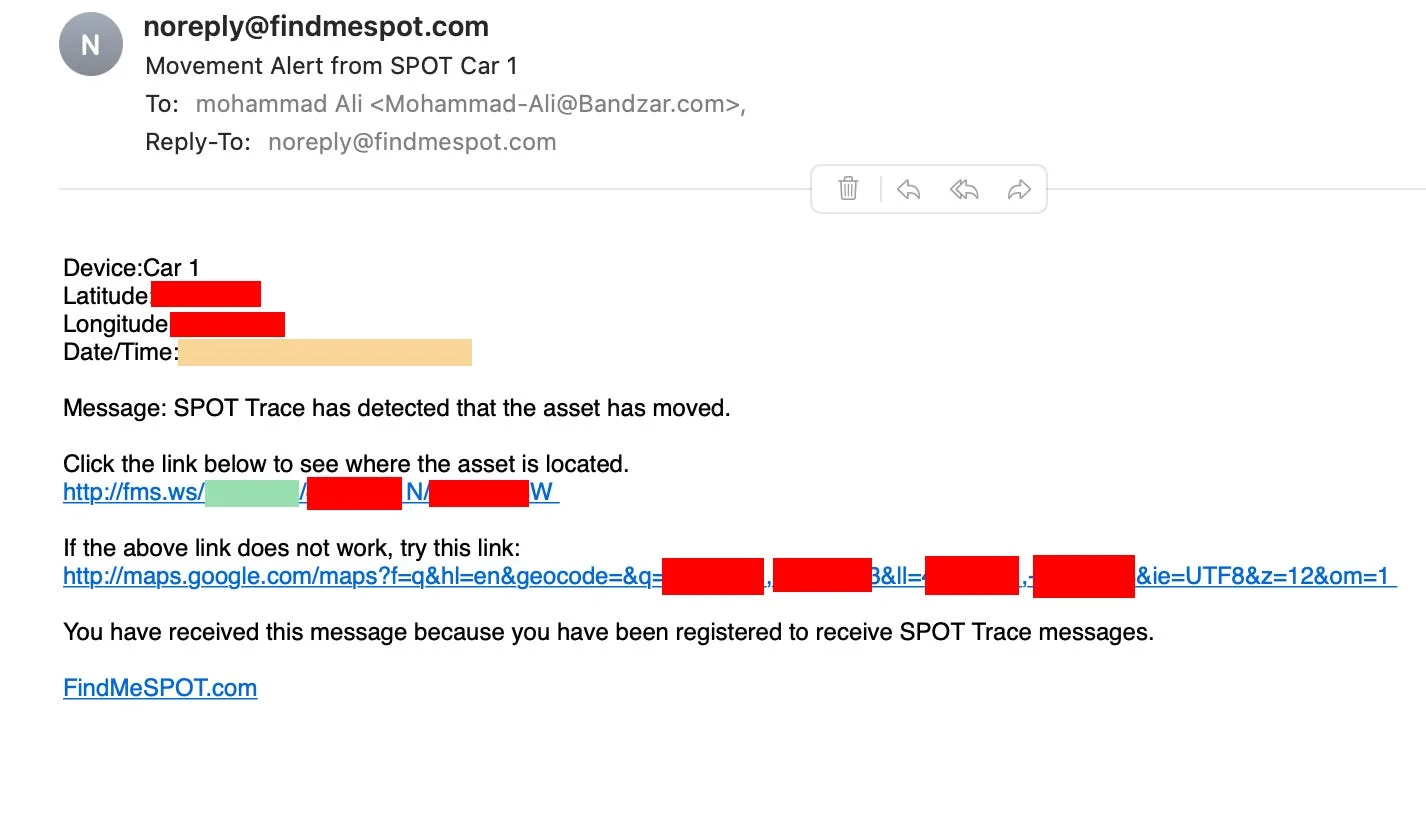
SPOT notification emails contain a shortened URL for their device location viewer.
http://fms.ws/1ghEAD/46.02296N/6.77219W
This redirects to:
https://www.findmespot.com/en-us/mylocation?id=1ghEAD/46.02296N/6.77219W
The URL contains two components:
1ghEAD: A message ID identifying the location transmission46.02296N/6.77219W: GPS coordinates in the URL path
The Vulnerability
When I modified the coordinates in the URL, I noticed a discrepancy: the site displayed the coordinates from the URL, but the embedded map showed a different location entirely.
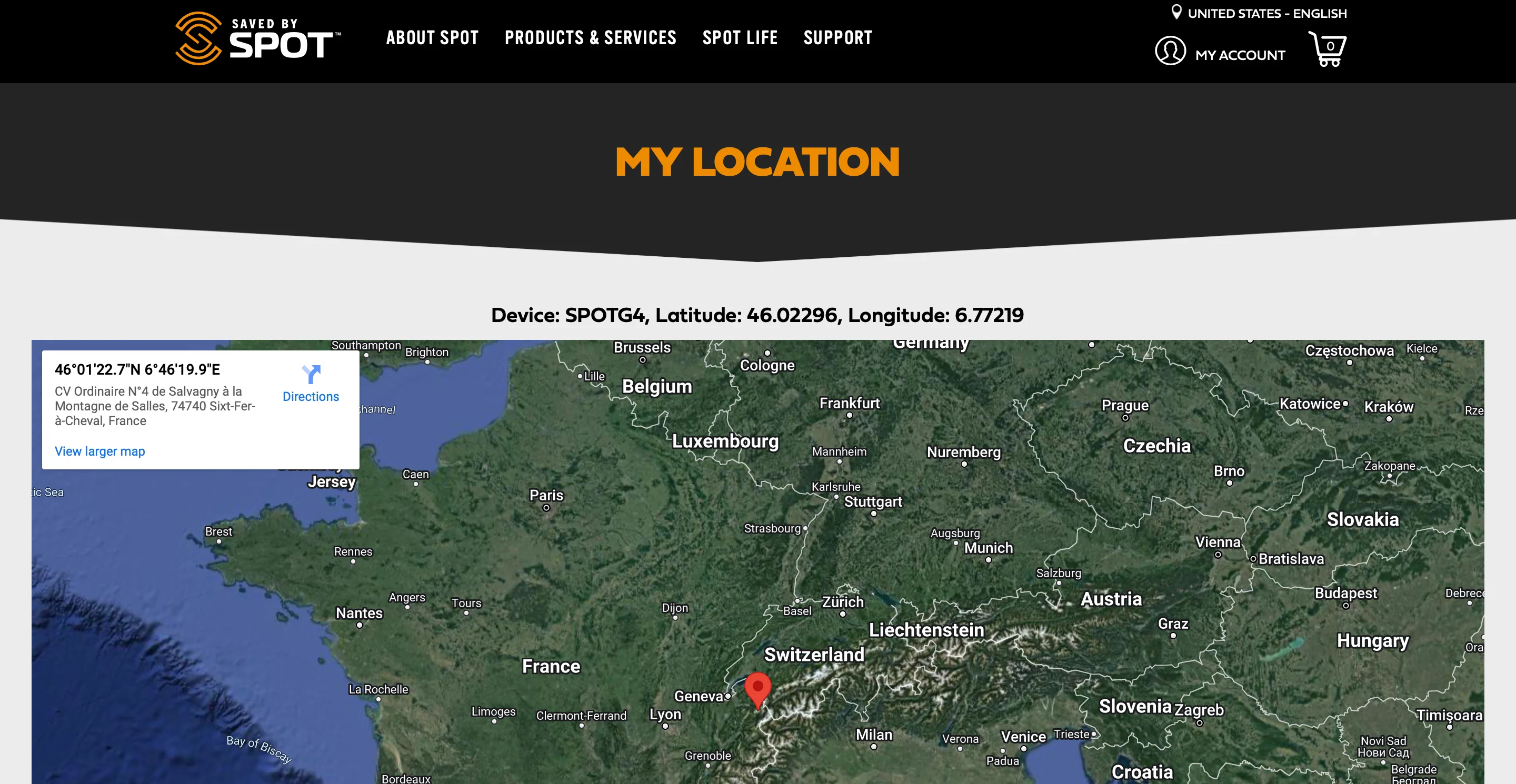
This revealed a critical flaw: Changing the message ID returned the location and device type of other people’s devices, exposing an IDOR vulnerability.
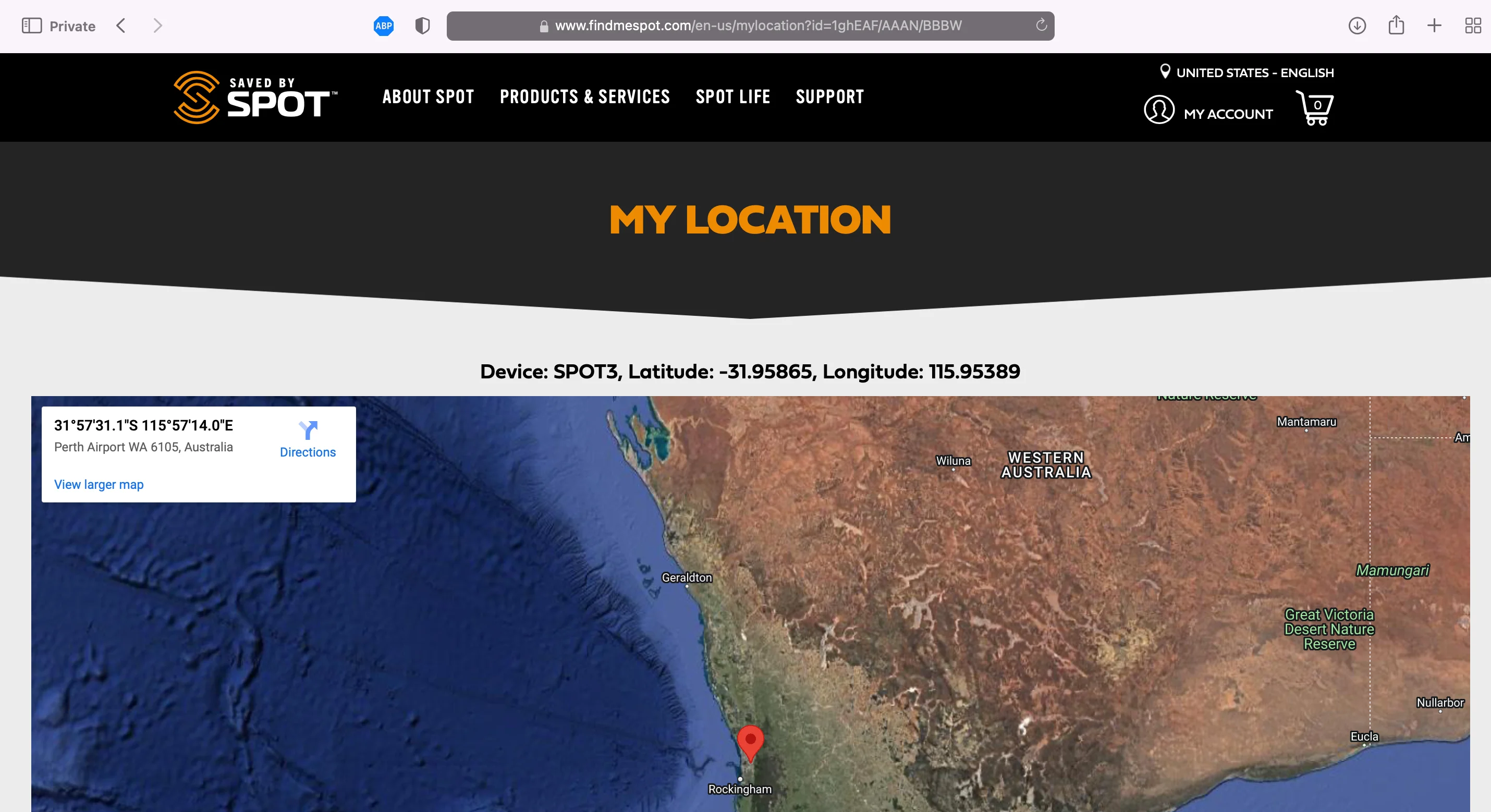
This vulnerability is compounded by the small keyspace: message IDs are short alphanumeric strings (typically 6 characters), making enumeration highly feasible. With no authentication required, an attacker could systematically iterate through message IDs to retrieve device locations and identify device types (SpotG4, Spot Trace, Spot X) for devices worldwide.
Impact
This vulnerability exposed real-time location data for devices worldwide. Individual users—hikers, travelers, and adventurers relying on SPOT for safety—had their locations exposed to anyone who could enumerate message IDs. This created risks of stalking and harassment. Attackers could also identify the exact location of valuable equipment left in remote areas, facilitating theft.
For businesses using SPOT to track fleet vehicles and shipping containers, the vulnerability exposed corporate logistics data including shipping routes, asset movements, and operational patterns that competitors could exploit.
The Fix
I reported this vulnerability to SPOT/Globalstar through their customer support portal. The vendor implemented an elegant backwards-compatible fix.
Since the URL already included coordinates in the path, but the server was ignoring them and only querying by message ID. The fix validates that the coordinates in the URL match the message ID’s stored location in the database.
This solution:
- Preserves all existing legitimate notification links (coordinates already match)
- Prevents enumeration (attackers don’t know correct coordinates for other message IDs)
- Requires no URL structure changes
The necessary additional entropy was already present in every URL—it simply needed to be checked.
Conclusion
This vulnerability illustrates a fundamental security principle: all inputs should be validated, regardless of their apparent purpose. The coordinates were present in every URL but ignored, enabling enumeration despite the server having validation data available.
The remediation demonstrates effective security design: leveraging existing data structures to implement validation without disrupting functionality or breaking existing links.